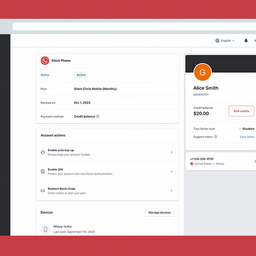
Launching Our New Dashboard
As a Silent Circle customer who uses our products to communicate securely with your team, you know about our dashboard. This is where you create accounts for your team, where you manage your plan and payments, where you add and remove telephone numbers,...